
Safeguard your digital assets with intelligent, compliant, and proactive cybersecurity. From regulatory audits to advanced threat simulations, our cybersecurity services are engineered to protect your systems, ensure regulatory alignment, and build long-term digital trust—across every industry we serve.
Meet the security and compliance standards set by RBI, IRDAI, SEBI, UIDAI, and other regulatory bodies. Our expert team performs in-depth penetration testing to uncover vulnerabilities, enhance resilience, and ensure your business stays secure and compliant — without disrupting day-to-day operations.
Identify vulnerabilities before attackers do. Simulate phishing, ransomware, and full-scope attacks through red teaming exercises designed to assess your real-world defenses.
Protect your digital assets through continuous vulnerability identification, analysis, and remediation. Our team uses industry-leading tools and methodologies to detect security weaknesses, assess risk levels, and help you strengthen your overall security posture before attackers can exploit them.
Detect, investigate, and respond to threats in real time with 24×7 monitoring and expert-led incident response. Our MDR team leverages advanced analytics, threat intelligence, and behavioral detection to quickly identify suspicious activity, contain attacks, and minimize business impact — keeping your environment secure around the clock.
Strengthen your organization’s credibility and security posture by achieving globally recognized standards and certifications. Our experts assist you in meeting compliance requirements such as ISO 27001, SOC 2, PCI DSS, GDPR, and other regulatory frameworks. From gap assessments and documentation to audit readiness and certification support, we ensure your business remains secure, compliant, and audit-ready at all times.
Identify, analyze, and mitigate potential threats before they impact your business. Our Risk Assessment & Management services help you understand your organization’s exposure across people, processes, and technology. We evaluate security controls, assess business impact, and develop actionable mitigation strategies — empowering you to make informed decisions, reduce risk, and enhance overall resilience.

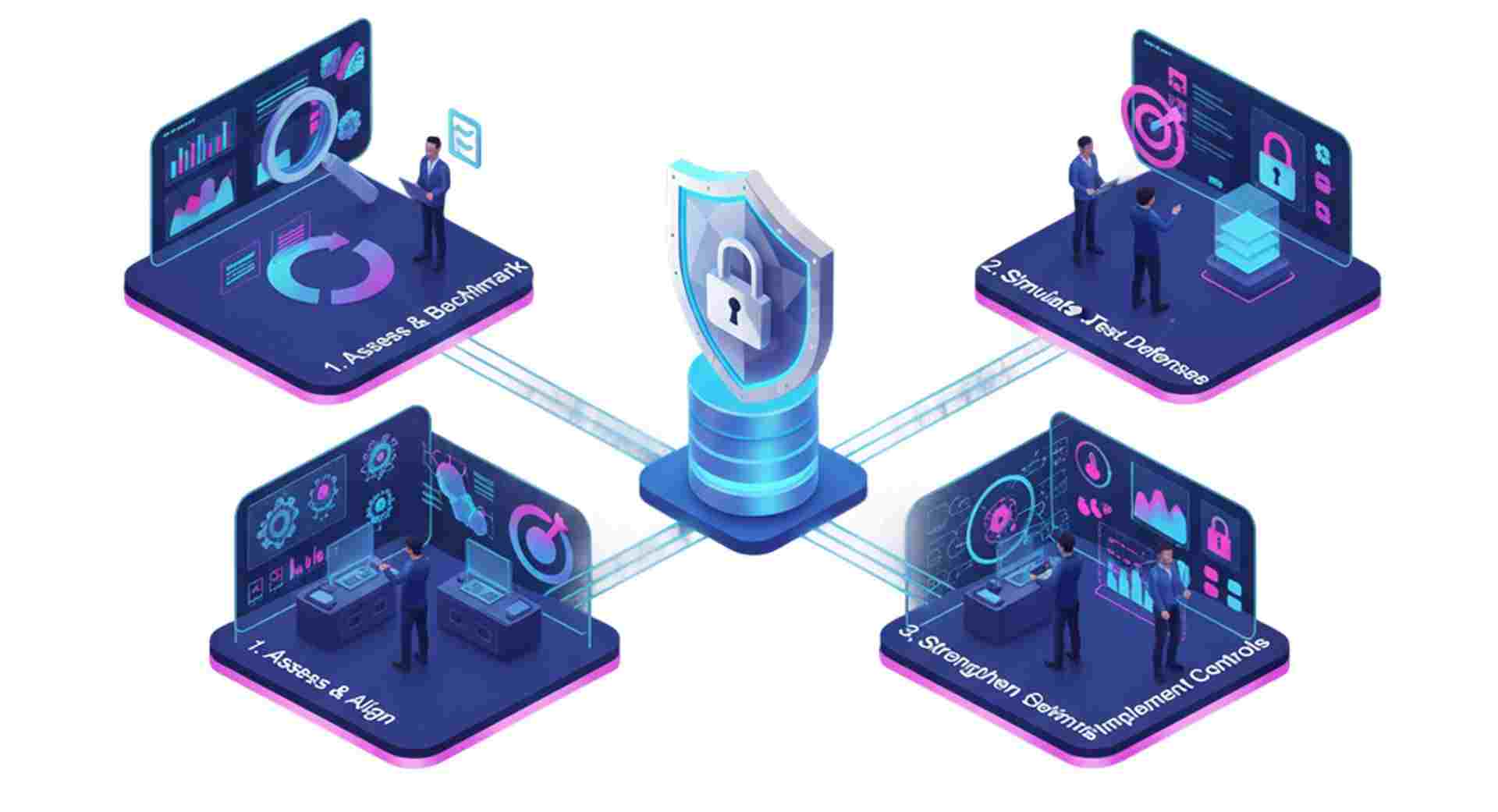
Our step-by-step model helps organizations secure their digital ecosystem by combining regulatory readiness, real-world threat defense, and continuous improvement — all aligned with business goals.
We begin by thoroughly evaluating your current security posture, identifying risks, gaps, and regulatory obligations across infrastructure, applications, and third parties.
Before real attackers strike, we simulate advanced threats to uncover vulnerabilities across endpoints, networks, and applications.
With insight in hand, we help you build or improve security controls to actively defend against real threats and reduce your attack surface.
Security doesn’t stop at implementation. We provide ongoing support to monitor threats, respond quickly, and adapt to new risks as they emerge.

We secure what matters most is your data, systems, and reputation. Our cybersecurity services are built on real-world expertise, regulatory mastery, and a zero-compromise mindset that helps enterprises stay ahead of evolving threats.
Our services ensure end-to-end compliance across industry regulations like ISO 27001, RBI, GDPR, SOC 2, and more. From audits to readiness assessments, we make compliance understandable and achievable - without unnecessary complexity.
With a threat-informed approach, we don’t just react to attacks - we stay ahead of them. Through red teaming, breach simulations, phishing assessments, and secure code reviews, we surface vulnerabilities early and eliminate blind spots.
Our strategies go beyond protection- they enable business continuity. By embedding real-time visibility, intelligent monitoring, and defined response frameworks, we build cyber resilience that grows with your organization.
We are trusted by organizations in highly regulated industries—banking, insurance, government, and technology. Our record reflects measurable impact, long-term client relationships, and security strategies that evolve with your needs.
Successful Incident Containments in the Past Year
Reduction in Breach Attempts for Managed Clients
Global Security Operations Monitoring
Audit Success Rate Across All Compliance Frameworks